Many companies with millions of users and sensitive information get hacked. This information will be exposed to the public, making it very risky for their users, such as passwords, credit card info, emails, and more because they don’t use the hash.
The thing wrong with these companies is that many of them don’t hash their user’s info, making it difficult to get the actual data and benefits from these lacked data. Fortunately, there is something called the hash that can fix this problem, and this article will explain this thing in detail.
1. Hashing
Hashing is one kind of cryptography science that converts any data like strings into another value using an algorithm that uses a specific mathematical calculation for every type of hashing.
It is worth noting that you can not decrypt this new value created from the string or restore its original value after hashing it, which means it is one way of encrypting the string.
In python, there are a lot of hashing libraries you can use in your code, such as bcrypt & hashlib but let’s first explore the last one and leave the bcrypt in another tutorial:
import hashlib
# Use The md5 Hash
hashing = hashlib.md5()
# Add Your Message
hashing.update(b"Thanks")
# Convert The Message To a Hexadecimal
print(hashing.hexdigest())When you execute the previous code, you will get a long string text, the hash value of the word “Thanks” using the md5 algorithm.
Notice that if you’ve used the same word I’ve used in this example, you will have the same result because this is so basic hashing algorithm.
2. The Available Hashing
There are better hashes that can perform better than the previous one, the weakest one md5 hash. Let’s see the available hashed for this hashlib library:
import hashlib
# Print The Availabe Hashes
print(hashlib.algorithms_guaranteed)You will have many different types of hashes, and my computer system is Linux which will give me this output:
{'shake_256', 'sha1', 'blake2b', 'sha512', 'sha3_256', 'md5', 'blake2s', 'sha3_384', 'sha256', 'sha3_512', 'sha384', 'sha3_224', 'sha224', 'shake_128'}If you use macOS or Windows, you may get other different hashes according to your operating system.
3. Hashes Are Risky
Web developers need to learn to hash so they can use it to store the user’s passwords in the database so when it gets hacked, bad people can’t see the original password of their users.
Still, it can be risky if some users have used known passwords such as “qwerty” & “admin” & “123” as an example, to name a few because there are many online services that store the most commonly used passwords among people and their hashes, so they make brute-force on these hashes and get the areal password.
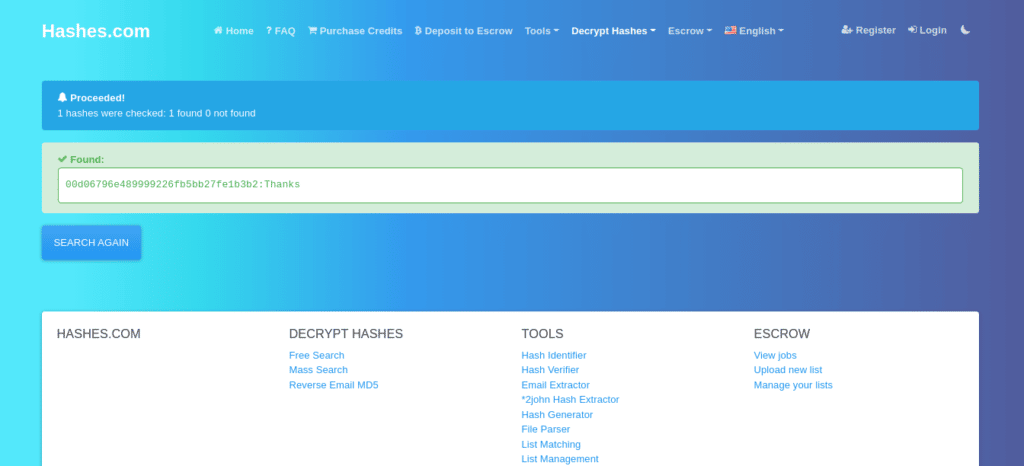
Let’s try another hash type and see if this website can find the actual values behind that hash:
import hashlib
# Use The md5 Hash
hashing = hashlib.sha512()
# Add Your Message
hashing.update(b"Thanks")
# Convert The Message To a Hexadecimal
print(hashing.hexdigest())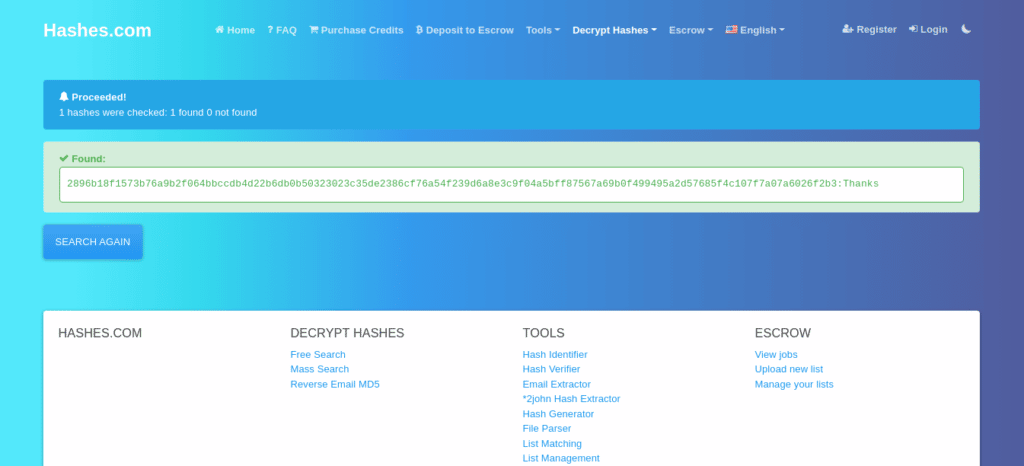
The website could get the actual value behind the sha512 hash we’ve used in the previous example. Suppose the user has used a long and weird password in your web application when signing up. The hackers can’t find the actual password behind this hash. Let’s see this new example:
import hashlib
# Use The md5 Hash
hashing = hashlib.md5()
# Add Your Message
hashing.update(b"hgsjhdjfkf")
# Convert The Message To a Hexadecimal
print(hashing.hexdigest())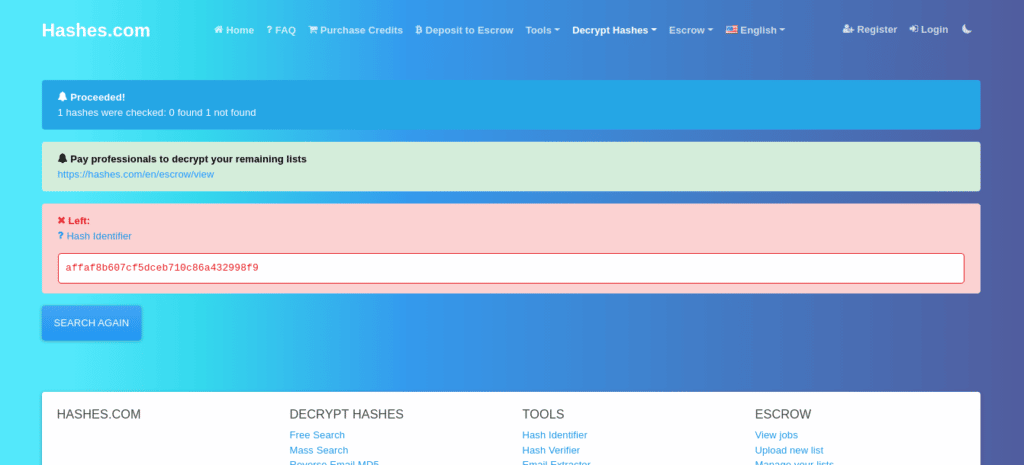
As you see from the previous image that the website couldn’t find the actual password behind this hash. Unfortunately, not all of your users do these best practices. So what’s the solution for this? Something is known as salt.
4. The Salt In Hashes
The salt is a random and robust value you will add to the word or password you want to hash to get a different output every time you use the same password.
This kind of action will help make your user password much stronger because if the hacker gets the actual password, he won’t be able to catch the other user’s password if they use the same word.
Another thing you can do to make the hashes even better and almost impossible for cracking is adding the round number, which means hashing the string many times. Let’s see a simple example about this:
import hashlib, binascii
# Generating The Hashing
hashing = hashlib.pbkdf2_hmac("md5", b"Thanks", b"salt", 1000000)
# Showing The Binary Data Hexadecimal Representation
print(binascii.hexlify(hashing))The previous example has used the .pbkdf2_hmac() function followed by many parameters. The first one is the hashing you will use, md5 in this example. Then you will specify the password, which is “Thanks” with the salt value and the number of rounds.
The salt value in this example was “salt” and you can use any value you want. The round number is 1000000, which means you will hash the password 1000000 times.
Cracking this password requires the attacker to know the password, salt value, and round number, making it almost impossible for them to crack it.
Notice that if you’ve used the same example above, you will have the same result as I got because we are using the same salt value and the same round number.
Conclusion
Every web developer needs to let the website generate different salt values for every password the user type to make it stronger as much as you can. Suppose you are a web developer using the Flask or Django framework. In that case, I will suggest looking for many other hashing libraries that are stronger and more popular than hashlib, but it is still suitable for this job.